The first email was sent in 1971 by Ray Tomlinson while working for ARPANET. Since then, billions upon billions of emails have been exchanged between colleagues, friends, family—and even complete strangers. Email remains one of the most widely used forms of written communication today.
There are an estimated 4 billion email users worldwide. While alternative communication tools like Slack (with 20 million daily users in 2019) are growing in popularity, they still can't compete with email. A staggering 300 billion emails are sent every day. Although a significant portion is spam or unwanted, the average office worker still receives around 120 emails per day, ranging from notifications and internal communications to project updates, marketing messages, and client correspondence.
Now that we’ve established email's continued dominance as the preferred tool for written communication—and with usage projected to rise—let’s take a closer look at how to use it safely and effectively.
Email in Office 365
Many businesses are now launching or migrating their email infrastructure to the cloud. One of the most popular cloud-based solutions is Office 365. When properly configured, Office 365 provides several benefits—but also some risks. Some risks are shared with on-premises servers, while others are specific to cloud-based platforms.
Below, we’ll walk through key email protocols and security considerations.
SMTP, IMAP, and POP3
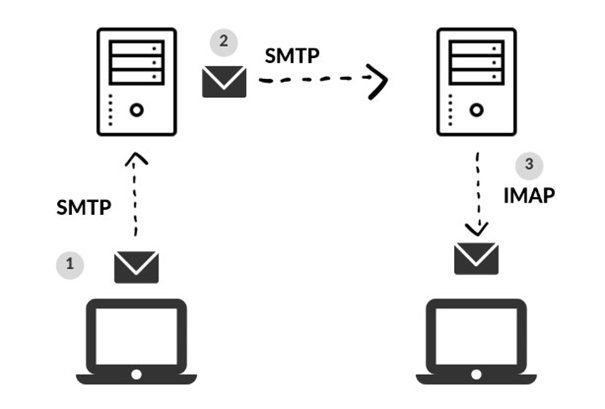
You've probably heard of SMTP, IMAP, and POP3—but what do these acronyms actually mean?
- SMTP (Simple Mail Transfer Protocol): The industry standard for sending email. SMTP is responsible for transmitting, relaying, or forwarding messages from a mail client to a receiving server.
- IMAP (Internet Message Access Protocol): Used for retrieving email from a server. IMAP syncs messages across devices, keeping emails stored on the server.
Together, SMTP and IMAP make email communication possible.
So, where does POP3 fit in?
- POP3 (Post Office Protocol version 3): Also retrieves emails, like IMAP—but with a key difference. POP3 downloads emails to the client and then deletes them from the server. This means emails are not synced across devices.
Mail Encryption
Exchange Online (part of Office 365) automatically encrypts mail between servers using TLS 1.2.
- Emails sent within the same Office 365 organization are encrypted by default.
- Emails sent to other Office 365 customers are also encrypted and secured with Forward Secrecy.
- By default, Exchange Online uses opportunistic TLS, meaning it attempts the highest level of encryption both parties support.
Mail Security
Modern email systems use several protocols to authenticate senders and reduce spoofing:
- SPF – Sender Policy Framework
- DKIM – DomainKeys Identified Mail
- DMARC – Domain-based Message Authentication, Reporting, and Conformance
Why do these matter?
Publishing SPF and DKIM records helps prevent spoofing and phishing by identifying which servers are authorized to send mail on behalf of your domain. DMARC instructs the receiving server on what to do if messages fail SPF or DKIM checks (e.g., mark as spam or reject).
Without these records, your emails may land in spam or be quarantined.
When configured correctly, Office 365 uses advanced machine learning to filter spam and phishing messages. It also runs SPF and DKIM checks. While this improves security, it can also produce false positives—legitimate emails flagged as threats. If you’re missing emails that were confirmed as sent, check with your admin. They may be stuck in quarantine.
Office 365 also offers Data Loss Prevention (DLP) policies aligned with standards like PCI DSS, GDPR, and HIPAA, helping prevent the unintentional sharing of sensitive data.
If Office detects repeated policy violations, your mailbox may be locked to protect company information.
Lastly, remember:
- Don’t use your corporate email for personal use.
- All communication is subject to review and may be reassigned if your account is converted to a shared mailbox after departure.
Email and Information Security
As the primary tool for business communication, email presents a range of security risks beyond phishing and spam. Let’s explore some lesser-known threats.
Probing
Every day, millions of new email accounts are created and abandoned. People often make new accounts to try a service, avoid spam, or start fresh. Business accounts are also deactivated as employees come and go.
Risks of Unauthorized Access
If someone gains access to your inbox, it's not just your messages at stake. Here’s what a hacker can do:
- Lock you out by changing your password
- Impersonate you to extract sensitive info from contacts
- Access cloud-stored files via email links
- Change settings (e.g., language, themes) or delete messages
- Send damaging emails under your name
- Set up auto-forwarding rules to spy on future emails
- Mine historical emails for confidential data
- Sign you up for services using your address
- Reset passwords and take over other accounts
- Use stored credit card details to make purchases
Thankfully, email security has improved significantly. Today, features like multifactor authentication, location-based login verification, and recovery email addresses help reduce the risk.
Conclusion
Since the first email was sent over 50 years ago, the security, availability, and storage capacity of email systems have evolved tremendously. Today, email remains the preferred method of communication in the business world—but only when used safely and responsibly.
By understanding how email works and taking advantage of modern security protocols and tools, users and organizations alike can significantly reduce risks and protect sensitive information.










